We knew it was coming last week and here it is. The Enterprise and Mobility Security blog announced that the Azure Active Directory Domain Services are now generally available today. Program Manager Mahesh Unnikrishnan wrote a guest blog to give us a look at the officially released features.
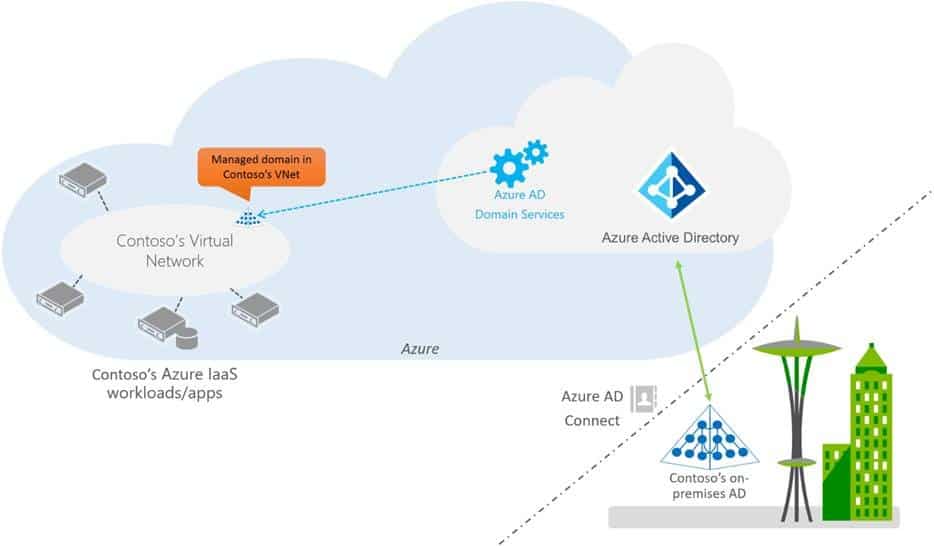
For a reminder, the Azure AD Domain Services is a domain controller that lets you set up your own with an Azure virtual machine. You can use your already established Active Directory, LDAP, NTLM, or Kerberos credentials. Once logged in, the domain services let you move on-premises apps to Azure cloud quickly, develop and test, and securely manage multiple virtual machines with Group Policy.
After nearly a year of work since the first preview, Mahesh shared a list of key features that have been added since last October.
- Support for secure LDAP: You can access your managed domain using LDAPS (secure LDAP), including over the internet.
- Custom OU support: Users in the ‘AAD DC Administrators’ delegated group can create and administer a custom organizational unit on your managed domain.
- Configure managed DNS for your domain: Users in the ‘AAD DC Administrators’ delegated group can administer DNS on your managed domain using Windows Server DNS administration tools.
- Domain join for Linux: We’ve worked with RedHat to document how you can join a RedHat Linux VM to your managed domain.
- New and improved synchronization with your Azure AD tenant: We have re-designed the synchronization between your Azure AD tenant and your managed domain. For existing domains, this new improved synchronization has been rolled out automatically in a phased manner.
- The ‘password does not expire’ attribute: Some accounts had the ‘password-does-not-expire’ attribute set on them, for example, service accounts. The password policy was being enforced for these accounts in managed domains, resulting in their passwords expiring. Passwords for such accounts will not expire.
- Incorrect group display name for accounts created in Azure AD: The samAccountName attribute for groups created in Azure AD was not being set correctly in the managed domain. These were being set to GUIDs instead of valid samAccountName.
- SID history sync: The on-premises primary user and group SIDs will now be synchronized to your managed domain and set as the SidHistory attribute on corresponding users and groups. This cool feature helps you lift-and-shift your workloads to Azure without having to worry about re-ACLing them.
- Virtual network peering: The Azure networking team recently announced GA for virtual network peering. This awesome feature makes it easy to connect Domain Services to other virtual networks. You can connect a classic virtual network in which your managed domain is available to workloads deployed in resource manager virtual networks using network peering.
According to Mahesh, there were over 5,700 tenants testing the domain services in the preview program. Thanks to their feedback, a batch of features were introduced before the public release. They enabled improved the management of AAD DC Administrators to configure DNS and create custom organizational units. Likewise, they added support for LDAP access and made sure that it was secure, of course.
Want to learn more about the Azure AD Domain Services? Check out the product page.